ebs: central Configuration
To configure ebs for use with external authentication, there are several configuration steps that must be completed in ebs: central:
The OIDC Issuers screen contains the reference data for configuring Microsoft Entra ID and Google Workspace.
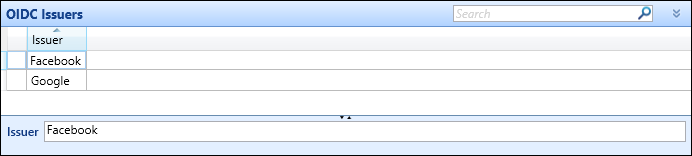
Complete the following:
-
Set a unique Issuer name (for example: AzureAD or Google Workspace).
-
Set the ebs Property and Claim Name based on the information that you wish to match
Note: Properties chosen must not be mutable, and must not be modifiable by the end user.
-
College Email (PEOPLE.COLLEGE_EMAIL) (for example: claim name email)
-
External Identifier (EXTERNAL_IDENTIFIERS.ID)
-
Person Code (PEOPLE.PERSON_CODE)
-
User ID (USERS.ID)
-
Username (USERS.NAME)
-
Note: You must enter properties that uniquely identify the person in both ebs and externally. When matching on properties, if a match cannot be made or there are multiple records in ebs with the same match information, authorisation to ebs will be refused.
The Identity Server screen contains the institution settings for configuring Microsoft Entra ID and Google Workspace.
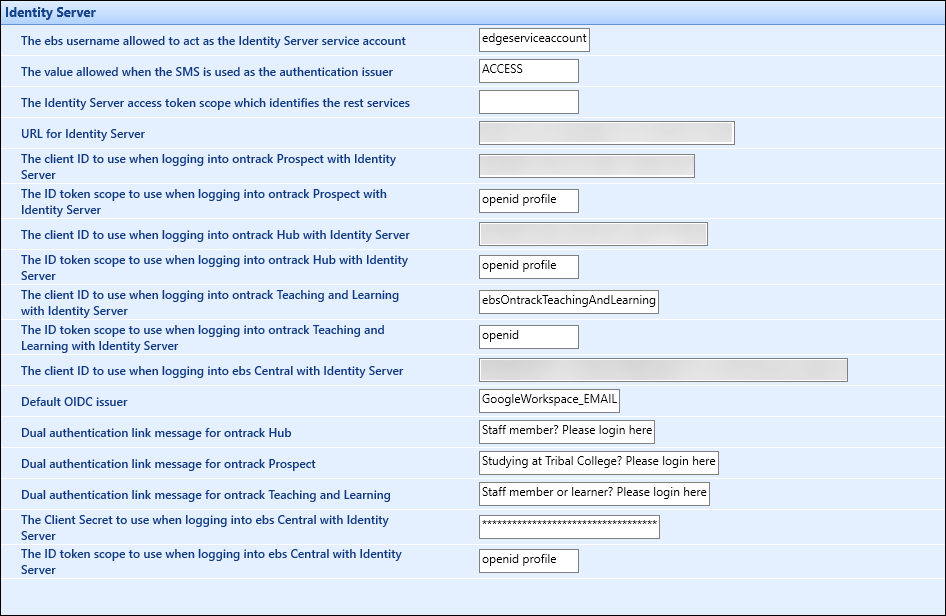
Enter the following values.
| This field | Enter this information... |
|---|---|
| The Identity Server access token scope which identifies the rest services | The Identity Server access token scope which identifies the rest services. This field should be left blank. |
| URL for Identity Server |
The URL for the Identity Server.
|
| The client ID to use when logging into ontrack Prospect with Identity Server |
The client ID for the appropriate ontrack website setting.
|
| The ID token scope to use when logging into ontrack Prospect with Identity Server |
The ID token scope for the appropriate ontrack website setting.
|
| The client ID to use when logging into ontrack Hub with Identity Server |
The client ID for the appropriate ontrack website setting.
|
| The ID token scope to use when logging into ontrack Hub with Identity Server |
The ID token scope for the appropriate ontrack website setting.
|
| The client ID to use when logging into ontrack Teaching and Learning with Identity Server |
The client ID for the appropriate ontrack website setting.
|
| The ID token scope to use when logging into ontrack Teaching and Learning with Identity Server |
The ID token scope for the appropriate ontrack website setting.
|
| The client ID to use when logging into ebs Central with Identity Server |
The client ID to use when logging into ebs: central with Identity Server. Note: Refer to ebs Client Authentication for Microsoft Entra ID for further information. |
| Default OIDC issuer | The issuer name defined during Microsoft Entra ID or Google Workspace configuration |
| Dual authentication link message for ontrack Hub | If dual authentication is being used, enter the link message. |
| Dual authentication link message for ontrack Prospect | If dual authentication is being used, enter the link message. |
| Dual authentication link message for ontrack Teaching and Learning | If dual authentication is being used, enter the link message. |
| The Client Secret to use when logging into ebs Central with Identity Server | The client secret. |
| The ID token scope to use when logging into ebs Central with Identity Server |
The ID token scope to use when logging into ebs: central with Identity Server. Note: Refer to ebs Client Authentication for Microsoft Entra ID for further information. |
A user record is required to authenticate with an external provider.
To create a user record with User Management:
-
Search for the relevant user.
-
Click the Create User button on the Admin Commands ribbon..
The Create User window is displayed.

-
Enter the relevant details, including:
-
Username
-
Authentication Type - select 'Active Directory' from the drop-down list
-
-
Click Save.
Note: Refer to Creating user records for further details of how to create user records.